影响版本
Linux内核 2.6.19-rc1~5.12-rc8
Alibaba Cloud Linux 2/3、CentOS 7/8、RedHat 7/8、Ubuntu 14/16/18/20、Debian 8/9/10、SUSE Linux Enterprise Server 12/15、OpenSUSE 42.3/15
漏洞原理
利用内核级网络组件的堆溢出缺陷,突破容器依赖的内核隔离机制(命名空间等),从受限制的容器环境获取宿主机权限。
Netfilter模块在处理32位进程的sockopt请求时发生堆溢出,攻击者通过堆喷(Heap Spraying)和UAF(Use-After-Free)技术控制内核内存,执行ROP链提权至root权限。
环境搭建
1
2
3
4
5
6
7
8
9
10
11
12
|
proxychains4 wget https://dl.lamp.sh/kernel/el7/kernel-ml-5.10.48-1.el7.x86_64.rpm
proxychains4 wget https://dl.lamp.sh/kernel/el7/kernel-ml-devel-5.10.48-1.el7.x86_64.rpm
proxychains4 wget https://dl.lamp.sh/kernel/el7/kernel-ml-headers-5.10.48-1.el7.x86_64.rpm
yum localinstall kernel-ml-* --skip-broken
awk -F\' '$1=="menuentry " {print i++ " : " $2}' /etc/grub2.cfg
grub2-set-default 1
reboot
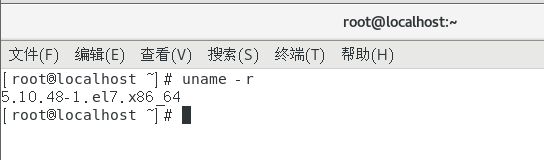
uname -r
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
| FROM centos:7
RUN rm -f /etc/yum.repos.d/*.repo && \
echo "[base]" > /etc/yum.repos.d/CentOS-Base.repo && \
echo "name=CentOS-7 - Base" >> /etc/yum.repos.d/CentOS-Base.repo && \
echo "baseurl=http://vault.centos.org/7.9.2009/os/\$basearch/" >> /etc/yum.repos.d/CentOS-Base.repo && \
echo "gpgcheck=1" >> /etc/yum.repos.d/CentOS-Base.repo && \
echo "gpgkey=http://vault.centos.org/7.9.2009/os/\$basearch/RPM-GPG-KEY-CentOS-7" >> /etc/yum.repos.d/CentOS-Base.repo && \
\
echo "[updates]" >> /etc/yum.repos.d/CentOS-Base.repo && \
echo "name=CentOS-7 - Updates" >> /etc/yum.repos.d/CentOS-Base.repo && \
echo "baseurl=http://vault.centos.org/7.9.2009/updates/\$basearch/" >> /etc/yum.repos.d/CentOS-Base.repo && \
echo "gpgcheck=1" >> /etc/yum.repos.d/CentOS-Base.repo && \
echo "gpgkey=http://vault.centos.org/7.9.2009/os/\$basearch/RPM-GPG-KEY-CentOS-7" >> /etc/yum.repos.d/CentOS-Base.repo && \
\
echo "[extras]" >> /etc/yum.repos.d/CentOS-Base.repo && \
echo "name=CentOS-7 - Extras" >> /etc/yum.repos.d/CentOS-Base.repo && \
echo "baseurl=http://vault.centos.org/7.9.2009/extras/\$basearch/" >> /etc/yum.repos.d/CentOS-Base.repo && \
echo "gpgcheck=1" >> /etc/yum.repos.d/CentOS-Base.repo && \
echo "gpgkey=http://vault.centos.org/7.9.2009/os/\$basearch/RPM-GPG-KEY-CentOS-7" >> /etc/yum.repos.d/CentOS-Base.repo
RUN yum clean all && yum makecache && \
yum install -y gcc gcc-c++ make glibc-devel.i686 glibc-static.i686 libstdc++-devel.i686
RUN mkdir -p /cve-2021-22555
COPY exploit.c /cve-2021-22555/
WORKDIR /cve-2021-22555
RUN gcc -m32 -static -std=c99 -o exploit exploit.c
CMD ["/bin/bash"]
|
1
| proxychains4 docker build -t cve-2021-22555:latest .
|
漏洞复现
POC
漏洞利用需要容器具备特定权限:--privileged和--cap-add=NET_ADMIN是必要的,因为漏洞涉及网络命名空间操作
1
| docker run -it --rm --privileged --cap-add=NET_ADMIN --security-opt apparmor=unconfined cve-2021-22555:latest
|
1
2
3
|
cd /cve-2021-22555
./exploit
|
漏洞利用成功率并非 100%,可能需要多次尝试(建议尝试 3-5 次)
成功利用后会显示 “got root!” 并获取 root 权限,可通过id命令验证。
修复建议
CentOS/RHEL 7kernel-3.10.0-1160.36.2.el7 或更高
CentOS/RHEL 8kernel-4.18.0-348.2.1.el8_5 或更高
Ubuntu 20.04linux-image-5.4.0-91-generic 或更高
内核主线(mainline)5.12.1 及以上







